As of July 7, 2021, Microsoft has issued an emergency security update for Windows to address CVE-2021-34527, known as PrintNightmare.
About the vulnerability
The vulnerability in the Windows Print Spooler service was discovered by a group of security researchers working for the Chinese information security firm Sangfor Technologies. If exploited, it allows a standard user to execute code as SYSTEM to compromise Active Directory domain controllers. It involves the RpcAddPrinterDriverEx() function that facilitates the installation of print drivers.
This is said to be related to, but not the same as, CVE-2021-1675 – another RCE vulnerability in the spool service fixed in the June Patch Tuesday updates. Initially, it was labelled as a privilege escalation issue, but later upgraded to RCE at which point proof of concept exploitation code was published by security researchers, as they believed the issue was resolved.
A key mistake
Unfortunately, the proof of concept exploitation code was not for the patched CVE-2021-1675, but instead was for PrintNightmare. Whist the code was quickly removed, various forks and copies remain available. And the main concern focuses on domain controllers – but in practice, any Windows machine which has the targeted service enabled is at risk, particularly those using Point and Print. The service is enabled by default.
Suggested mitigations
Whilst Microsoft has issued an emergency patch, it does not signify the end of the matter. The patch still leaves open a hole that allows for a local privilege escalation attack.
Windows admins are advised to take immediate action. The issue is so serious, some university students are being advised to disable the service on home computers (source: author is a University student).
However, if you have a personal Windows device, we strongly recommend that you disable the Windows print programme – called ‘Windows Print Spooler’ – to protect your device.
Official University email
Disable Print Spooler
To safely mitigate the issue, it is advised to disable the Print Spooler service. Note that this will restrict the ability to print.
To do this, you can search for services.msc in Windows Search or via Run, find the Print Spooler, click Stop and set the start-up type to disabled, as shown below.
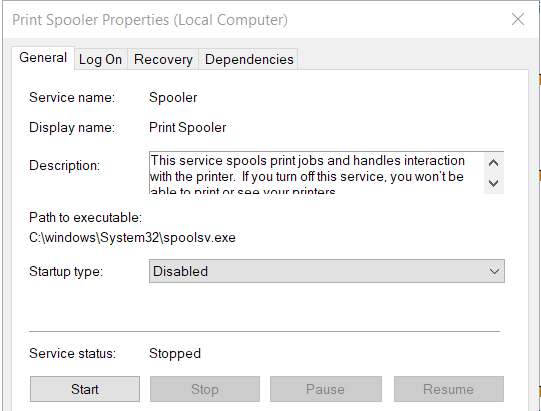
The code to achieve this in PowerShell follows:
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType DisabledBlock inbound print connections
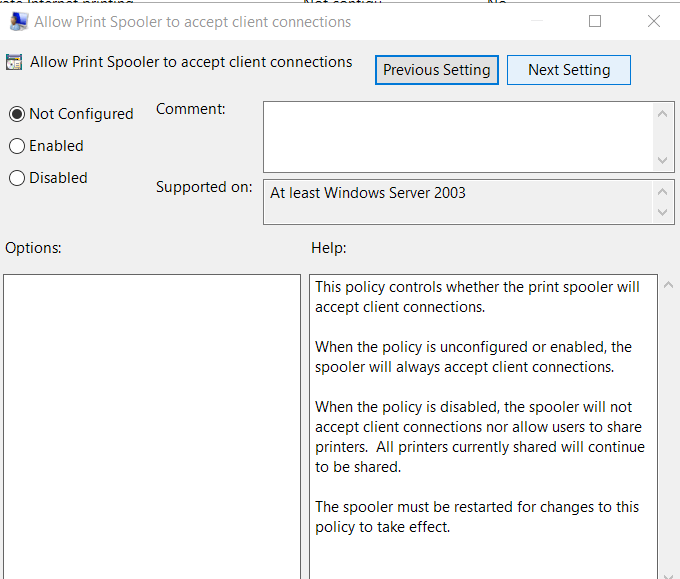
Alternatively, it is advised to disable inbound print connections via Group Policy where possible (in cases where the Spooler cannot be disabled). This mitigation will still allow local printing.
Patch issued
It is advisable to install the latest out-of-band patch for Windows devices which resolves the RCE issue. As of writing, the patch is not yet available for Windows 10 version 1607, Windows Server 2016, or Windows Server 2012, which are also affected.
Resources
The following is a list of verified sources of information, including links to the patch.
- Official Microsoft notice for the similar, but older CVE-2021-1675 – https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-1675
- Official Microsoft notice for PrintNightmare (CVE-2021-34527) [Includes patch download] – https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527
- Windows Update information (page for Windows 10 21H1) – https://support.microsoft.com/en-us/topic/july-6-2021-kb5004945-os-builds-19041-1083-19042-1083-and-19043-1083-out-of-band-44b34928-0a71-4473-aa22-ecf3b83eed0e
- US Government CISA Information – https://us-cert.cisa.gov/ncas/current-activity/2021/06/30/printnightmare-critical-windows-print-spooler-vulnerability and https://us-cert.cisa.gov/ncas/current-activity/2021/07/06/microsoft-releases-out-band-security-updates-printnightmare
- CERT Vulnerability information – https://www.kb.cert.org/vuls/id/383432
- MITRE CVE Page for PrintNightmare – https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-34527
- Proof of Concept (C++) – https://github.com/afwu/PrintNightmare
- Proof of Concept (Python) – https://github.com/cube0x0/CVE-2021-1675
- Proof of Concept (PowerShell) – https://github.com/calebstewart/CVE-2021-1675